Beginner's Guide to Understanding Computer Networks
Reasons to Explore Computer Network Fundamentals
Machines are expensive applications and this applications have high latency and may require more CPU ,RAM,GPU and other resources for the applications to run, causing high bills in cloud environment. Separation of the applications into components ,thus making the study , engineering and research and development process simpler. Expensive workloads are done on the server side.Client calls servers to perform expensive tasks.Remote procedural Calls implementation and usage is very important in many cases. Generally Servers have beefy hardware and clients have commodity hardware.Clients generally performs light-weight tasks where the binaries are smaller and edge computing could be another case.Clients can obtain dependencies from somewhere. To establish communication between Client side and Server-Side , the knowledge of computer networks and models like the Open System Interconnected Model has a very important role along with the knowledge of Application Programming Interface. The flow of data and monitoring of network systems is very crucial for providing good software products.This communication of Client and server is known as Client Server Communication. We are going to talk about Rules, Protocols followed while building up entire network systems for web applications. File Systems , Mail Systems and Printer servers are connected on some network with workstations. The network is entrusted to some other server . The server is responsible for authentication. User’s trust on Workstations.Trust on the server.
INTERNET is NETWORK OF NETWORKS . In a Network we have many interconnected devices like Routers ,Switches,Hubs and devices like mobile phone and Laptop and also Physical buses ,coaxial cables and wires sometimes for closer devices to establish communication among devices. We have the concept of Wide Area Network, Local Area Network , Metropolitan Area Network and many more. Internet is assumed to be a Giant Matrix that physically interconnects networks .
HOW INTERNET WORKS
There are two main concepts that are fundamental to the way the Internet functions: packets and protocols.
Packets
In networking, a packet is a small part of a larger message. Each packet contains both data and details about that data. The details about the packet's contents are called the "header," and it is placed at the front of the packet so the receiving machine knows how to handle it. To understand the purpose of a packet header, think of how some consumer products come with assembly instructions.
When data is sent over the Internet, it is first broken into smaller packets and then converted into bits. These packets are directed to their destination by networking devices like routers and switches. Once the packets arrive, the receiving device reassembles them in the correct order, allowing the data to be used or displayed. There is a Maximum Transmission Unit, which is the largest packet size that can be sent over a network.
Compare this process to how the Statue of Liberty was constructed. The statue was originally designed and built in France. However, it was too large to fit on a ship, so it was sent to the United States in pieces, along with instructions on where each piece should go. Workers who received the pieces put them together to form the statue that stands in New York today.
While assembling the Statue of Liberty took a long time, sending digital information in smaller pieces is extremely fast over the Internet. For example, a photo of the Statue of Liberty stored on a web server can travel across the world one packet at a time and load on someone's computer in just milliseconds.
Packets are sent across the Internet using a method called packet switching. Routers and switches in the network handle each packet separately, without considering where they come from or where they are going. This design prevents any single connection from taking over the network. If data were sent all at once between computers without packet switching, a connection between two computers could tie up multiple cables, routers, and switches for several minutes. This would mean only two people could use the Internet at a time, instead of the nearly unlimited number of people who can use it today.
PROTOCOLS
The development of the Internet faced a significant challenge: enabling communication between computers with diverse hardware and software configurations. To overcome this hurdle, a common language or set of rules was necessary, allowing devices to understand each other, much like people from different backgrounds need a shared language to communicate.
The solution to this problem lies in standardized protocols, which are uniform methods for performing specific actions and formatting data. These protocols enable devices to communicate and comprehend each other, facilitating seamless interaction.
A range of protocols has been established to govern various aspects of online communication. For example, Ethernet protocols manage packet transmission within a network, while IP protocols facilitate packet transfer between networks. TCP protocols ensure that packets arrive in the correct order, and HTTP protocols format data for websites and applications. Additional protocols address routing, testing, and encryption, and alternative protocols, such as UDP, are used for specific types of content, like streaming video.
The widespread adoption of these standardized protocols enables the Internet to function universally, allowing any device to connect and communicate with others, regardless of its hardware or software configuration. This ensures that the Internet remains a cohesive and accessible network, where devices can interact and exchange information seamlessly.
NETWORK
A network refers to a collection of computers, servers ,mainframes , network devices ,or other devices connected to one another to allow sharing of data and resources.
Network Topologies like the Star Topology , Ring Topology Bus and Mesh Topology are essential way Network devices and Systems follow to communicate among themselves .
Router directs Data between Networks, Switch Connects devices between LAN , managing Data Traffic, and Modem modulates and demodulates signals for internet Connectivity.
Project ARPANET of U.S Military Defence : The Advanced Research Projects Agency Network (ARPANET) was the first wide-area packet-switched network with distributed control and one of the first computer networks to implement the TCP/IP protocol suite. Both technologies became the technical foundation of the Internet. The ARPANET was established by the Advanced Research Projects Agency (now DARPA) of the United States Department of Defence.
Have you wondered how clicking a link opens a Web page in Seconds?
To display the page, the data was sent over the Internet in thousands of data packets. These packets travelled through cables, radio waves, routers, and switches from our web server to your computer or device. Your computer or smartphone received the packets and passed them to your browser, which interpreted the data to show you the text you are reading now.
The specific steps involved in this process are:
DNS query: When your browser started to load this webpage, it likely first made a DNS query to find out the Cloudflare website's IP address.
TCP handshake: Your browser opened a connection with that IP address.
TLS handshake: Your browser also set up encryption between a Cloudflare web server and your device so that attackers cannot read the data packets that travel between those two endpoints.
HTTP request: Your browser requested the content that appears on this webpage.
HTTP response: Cloudflare's server transmitted the content in the form of HTML, CSS, and JavaScript code, broken up into a series of data packets. Once your device received the packets and verified it had received all of them, your browser interpreted the HTML, CSS, and JavaScript code contained in the packets to render this article about how the Internet works. The whole process took only a second or two.


CLIENT-SERVER MODEL
Client-Server Model is a fundamental principle and computing model that facilitates communication and resource sharing between clients and servers. A client-server model have Workstations or client’s computer where the user-agent is present. An operating System platform like Windows, GNU/Linux and Mac OS should be there. Workstations initiate requests to Servers. Servers have Unix and Unix like operating Systems mostly like the AIX of IBM , Gentoo distributions and Ubuntu. Servers host and manage resources. Servers are beefy hardware with resources for computation. Server on the client side is a software installed in the client’s system. Servers host and manage resources. ServersTo display the page, the data was sent over the Internet in thousands of data packets. These packets travelled through cables, radio waves, routers, and switches from our web server to your computer or device. Your computer or smartphone received the packets and passed them to your browser, which interpreted the data to show you the text you are reading now.
The specific steps involved in this process are:
Domain Name Server query: When your browser started to load this web page, it likely first made a DNS query to find out the Cloud flare website's IP address.
TCP handshake: Your browser opened a connection with that IP address.
TLS handshake: Your browser also set up encryption between a Cloudflare web server and your device so that attackers cannot read the data packets that travel between those two endpoints.
HTTP request: Your browser requested the content that appears on this webpage.
HTTP response: Cloudflare's server transmitted the content in the form of HTML, CSS, and JavaScript code, broken up into a series of data packets. Once your device received the packets and verified it had received all of them, your browser interpreted the HTML, CSS, and JavaScript code contained in the packets to render this article about how the Internet works. The whole process took only a second or two. respond to client requests by providing data packets. Clients send requests to Servers. Servers host and manage resources. Servers processes the requests and return the requested data in the form of response . Servers respond to client requests by providing data packets. Communication requires the various network systems.
Characteristics of Client/Server Architecture
Asymmetrical protocols-There is a many-to-one relationship between clients and a server. Clients always initiate a dialog by requesting a service. Servers wait passively for requests from clients.
Encapsulation of services-The server is a specialist: when given a message requesting a service, it determines how to get the job done. Servers can be upgraded without affecting clients as long as the published message interface used by both is unchanged.
Integrity-The code and data for a server are centrally maintained, which results in cheaper maintenance and the protection of shared data integrity. At the same time, clients remain personal and independent.
Location transparency-The server is a process that can reside on the same machine as a client or on a different machine across a network. Client/server software usually hides the location of a server from clients by redirecting service requests. A program can be a client, a server, or both.
Message-based exchanges-Clients and servers are loosely-coupled processes that can exchange service requests and replies using messages.
Modular, extensible design-The modular design of a client/server application enables that application to be fault-tolerant. In a fault-tolerant system, failures may occur without causing a shutdown of the entire application. In a fault-tolerant client/server application, one or more servers may fail without stopping the whole system as long as the services offered on the failed servers are available on servers that are still active. Another advantage of modularity is that a client/server application can respond automatically to increasing or decreasing system loads by adding or shutting down one or more services or servers.
Platform independence-The ideal client/server software is independent of hardware or operating system platforms, allowing you to mix client and server platforms. Clients and servers can be deployed on different hardware using different operating systems, optimizing the type of work each performs.
Reusable code-Service programs can be used on multiple servers.
Scalability-Client/server systems can be scaled horizontally or vertically. Horizontal scaling means adding or removing client workstations with only a slight performance impact. Vertical scaling means migrating to a larger and faster server machine or adding server machines.
Separation of Client/Server Functionality-Client/server is a relationship between processes running on the same or separate machines. A server process is a provider of services. A client is a consumer of services. Client/server provides a clean separation of functions.
Shared resources-One server can provide services for many clients at the same time, and regulate their access to shared resources.
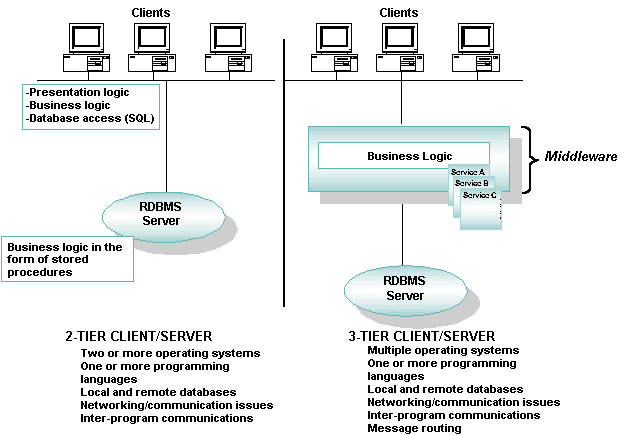
Differences Between 2-Tier and 3-Tier Client/Server Architectures
Every client/server application contains three functional units:
Presentation logic or user interface (for example, ATM machines)
Business logic (for example software that enables a customer to request an account balance)
Data (for example, records of customer accounts)
These functional units can reside on either the client or on one or more servers in your application. Which of the many possible variations you choose depends on how you split the application and which middleware you use to communicate between the tiers.
In 2-tier client/server applications, the business logic is buried inside the user interface on the client or within the database on the server in the form of stored procedures. Alternatively, the business logic can be divided between the client and server. File servers and database servers with stored procedures are examples of 2-tier architecture.
In 3-tier client/server applications, the business logic resides in the middle tier, separate from the data and user interface. In this way, processes can be managed and deployed separately from the user interface and the database. Also, 3-tier systems can integrate data from multiple sources.
2-Tier and 3-Tier Client/Server Models
Client/Server Variations to Suit Your Needs
Client/server architecture can accommodate the needs of each of the following situations:
Small shops and laptops-The client, the middleware software, and most of the business services operate on the same machine. We recommend this approach for one-person businesses such as a dentist's office, a home office, and a business traveller who frequently works on a laptop computer.
Small businesses and corporate departments-A LAN-based single-server application is required. Users of this type of application include small businesses, such as a medical practice with several doctors, a multi-department corporation, or a bank with several branch offices. In this type of application, multiple clients talk to a local server. Administration is simple: security is implemented at the machine level and failures are detected easily.
Large enterprises-Multiple servers that offer diverse functionality are required. Multiple servers can reside on the Internet, intranets, and corporate networks, all of which are highly scalable. Servers can be partitioned by function, resources, or databases, and can be replicated for increased fault tolerance or enhanced performance. This model provides a great amount of power and flexibility. How well you architect your application is critical to this client/server model. You may need to partition work among servers.
Data is a collection of facts, numbers , words , observations , statistical and mathematical representations that is required to learn something. Information is stored data in memory. Data can be audio,visual, image , video ,graphics or in some written format. Various devices need to communicate among them and transfer data from one device to another device. For example , We have a computer connected to a printer and we need to print some data like image. We need to ensure that there is proper communication between the printer and the computer .A copy of the Data is transferred from the sender i.e , the computer to the printer i.e., the receiver which has to print the image on the page.At the binary language level, this are basically combination of Zeroes and Ones.A Data Communication System is a setup that facilitates the exchange of data between devices or networks . This consists of five main components: Sender : The device that generates and sends the data. This depends on the reference of frame. Receiver: The device that receives the data.This depends on the reference of frame. Medium: The physical path through which data travels. Message: Message is the data that has to be transferred among various devices or networks. Protocol: The set of rules and conventions that determine how data is transmitted and received. For example, When we send an email, our computer(sender) sends the message through the internet (medium) using the email protocols, and the recipient’s computer (receiver) receives and processes it. This is because of the Data Communication System and the various components of the data communication system. Data communication links can be classified into different types, including: Wired links: These use physical cables, such as Ethernet or fiber optic cables, to connect devices. Wireless links: These use radio waves or other forms of electromagnetic radiation to connect devices, such as Wi-Fi or cellular networks. Point-to-point links: These connect two devices directly, such as a modem connection. Multi point links: These connect multiple devices, such as a local area network (LAN). Data communication links play a crucial role in modern communication systems, enabling the exchange of information between devices and facilitating various applications, such as: Internet communication: Email, web browsing, and online transactions. Network communication: File sharing, printing, and other network services. Telecommunication: Voice and video calls, messaging, and other forms of real-time communication.
The main components of Data Communication Link are as follows:
Message: The message that has to be transmitted is encrypted and sent via some medium from the sender. The receiver decrypts the data of the message. The message is modified in some way to prevent the noise from making any changes in the data. Message could be text, images or videos.
Sender: The device or system that initiates the transmission of the message such as computer or mobile phone.
Transmission Medium:The physical or logical path that the message travels through, such as :
I. Wired Medium: Coaxial Cables, Twisted pair Cables or fiber optic cables.
II. Wireless Medium: Radio Waves, Microwaves, infrared waves.
Receiver: The receiver receives the transmitted messages such as computer or phone.
Error detection and correction: Mechanisms to detect and correct errors that occur during transmission.
Protocols: A set of rules governing the transmission and reception of the message.
Flow control: Mechanisms to regulate the amount of the data that can be transmitted at one time.
Formatting: Mechanisms to format the data such as packetization.
Data Transmission Equipments: Devices that facilitate the transmission and reception of the message, such as:
I. Modems: Modulation or demodulation of the signals for transmission over wire or wireless medium.
II. Network Interface Cards: Connects devices to network and manage data transmission.
III.Routers: Connects multiple networks and manages data transmission between them. Layer Three Switches responsible for movement of packets from one point to another.
IV.Signal : The physical representation of the message, such as electrical signals, light waves, or radio waves.
V. Data Communication Link Diagram: The diagram presenting the Data Communication Links.
+---------------+
| Transmitter |
+---------------+
|
| Information
v
+---------------+
| Communication |
| Channel |
+---------------+
|
| Transmission Signal
v
+---------------+
| Receiver |
+---------------+
|
| Communication Rules
v
+---------------+
| Transmission |
| Devices |
+---------------+
CLIENT SERVER ARCHITECTURE:
The Client-Server Architecture Model is a fundamental design pattern in computer science that separates an application into two main components: a client and a server. In this model, the client requests services or resources from the server, and the server provides them. This architecture is widely used in various fields, including web development, networking, and distributed systems.
Key Components:
Client: The client is the component that requests services or resources from the server. It can be a web browser, a mobile app, or a desktop application. The client sends a request to the server, which then processes the request and returns a response.
Server: The server is the component that provides services or resources to the client. It can be a web server, a database server, or a file server. The server receives the request from the client, processes it, and sends a response back to the client.
How it Works:
Here's a step-by-step explanation of the client-server architecture model:
Request: The client sends a request to the server, specifying the service or resource it needs. This request can be in the form of an HTTP request, a database query, or a file request.
Server Receipt: The server receives the request and processes it. The server may need to authenticate the client, check for authorization, and validate the request.
Server Processing: The server processes the request, which may involve retrieving data from a database, performing calculations, or executing business logic.
Response: The server generates a response to the client's request. This response may include data, such as HTML pages, images, or files, or it may simply indicate the outcome of the request.
Client Receipt: The client receives the response from the server and processes it. The client may need to render the response, such as displaying a web page or playing a video.
Types of Client-Server Architecture:
There are several types of client-server architecture models, including:
One-Tier Architecture: In this model, the client and server are combined into a single component, and the application runs on a single machine.
Two-Tier Architecture: In this model, the client and server are separate components, and the application runs on two machines. This is the most common type of client-server architecture.
Three-Tier Architecture: In this model, the client, server, and database are separate components, and the application runs on three machines. This architecture is commonly used in web applications.
N-Tier Architecture: In this model, the application is divided into multiple tiers, each with its own set of components and responsibilities.
Advantages:
The client-server architecture model has several advantages, including:
Scalability: The client-server model allows for easy scalability, as new servers can be added to handle increased traffic.
Flexibility: The client-server model allows for flexibility in terms of the type of clients and servers used.
Security: The client-server model provides a secure way to access resources, as the server can authenticate and authorize clients.
Maintainability: The client-server model makes it easier to maintain and update applications, as changes can be made to the server without affecting the client.
Disadvantages:
The client-server architecture model also has some disadvantages, including:
Complexity: The client-server model can be complex to implement and manage, especially in large-scale applications.
Dependence on Server: The client-server model relies heavily on the server, which can be a single point of failure.
Network Latency: The client-server model can be affected by network latency, which can impact performance.
Security Risks: The client-server model can be vulnerable to security risks, such as hacking and data breaches.
Real-World Examples:
The client-server architecture model is widely used in various fields, including:
Web Development: Web applications, such as Facebook and Google, use the client-server model to provide services to users.
Online Banking: Online banking systems use the client-server model to provide secure access to banking services.
E-commerce: E-commerce websites, such as Amazon and eBay, use the client-server model to provide online shopping services.
Cloud Computing: Cloud computing services, such as AWS and Azure, use the client-server model to provide scalable and on-demand computing resources.
In conclusion, the client-server architecture model is a fundamental design pattern in computer science that provides a flexible and scalable way to build applications. While it has its advantages and disadvantages, it remains a widely used and effective model for building complex systems.
PURE ALOHA IN BRIEF:
Pure ALOHA is a simple multiple-access protocol used in wireless networks. Here's a brief illustration of the process:
1. Frame Arrival: A device (station) has data to send.
2. Transmission: The station sends the frame (data packet) immediately, without checking if the channel is busy.
3. Collision: If two or more stations transmit at the same time, a collision occurs, and the frames are destroyed.
4. Backoff: If a collision occurs, the station waits for a random amount of time before retransmitting the frame.
5. Retransmission: The station retransmits the frame after the backoff time.
6. Acknowledgment: If the frame is received successfully, the receiver sends an acknowledgment (ACK) to the sender.
7. Repeat: Steps 2-6 are repeated until the frame is successfully transmitted.
Pure ALOHA has a low throughput efficiency due to the high probability of collisions, especially in large networks. However, it is simple to implement and can be useful in small networks with low traffic.
Computer networks are made up of devices, protocols, and media that enable communication between different nodes.
TYPES OF NETWORKS:
Local Area Network: Local Area Network (LAN)
A Local Area Network (LAN) is a computer network that spans a small geographic area, such as a home, office building, or campus. It is a type of network that connects devices within a limited area, allowing them to communicate with each other and share resources.
Characteristics of LAN:
Geographic Scope: LANs typically cover a small area, such as a single building or campus.
Number of Devices: LANs usually connect a small number of devices, ranging from a few to several hundred.
Data Transfer Rate: LANs have high data transfer rates, typically in the range of 100 Mbps to 10 Gbps.
Network Topology: LANs often use a star or bus topology, where devices are connected to a central hub or switch.
Network Protocol: LANs use protocols such as Ethernet, Wi-Fi, or Token Ring to manage data transmission.
Types of LAN:
Wired LAN: A wired LAN uses physical cables, such as Ethernet cables, to connect devices.
Wireless LAN (WLAN): A wireless LAN uses radio waves to connect devices, eliminating the need for physical cables.
Virtual LAN (VLAN): A virtual LAN is a logical network that is created on top of a physical network, allowing multiple virtual networks to coexist on the same physical infrastructure.
Advantages of LAN:
High-Speed Data Transfer: LANs provide high-speed data transfer rates, making them ideal for applications that require fast data transfer.
Low Latency: LANs have low latency, making them suitable for real-time applications such as video conferencing and online gaming.
Reliability: LANs are generally more reliable than wide area networks (WANs), as they are less prone to errors and disruptions.
Security: LANs are typically more secure than WANs, as they are easier to manage and control.
Disadvantages of LAN:
Limited Geographic Scope: LANs are limited to a small geographic area, making them less suitable for applications that require wide area coverage.
Limited Scalability: LANs can be difficult to scale, as adding new devices can increase network complexity and reduce performance.
High Initial Cost: LANs can be expensive to set up, especially if a new infrastructure needs to be installed.
Real-World Applications of LAN:
Office Networks: LANs are commonly used in office buildings to connect computers, printers, and other devices.
Home Networks: LANs are used in homes to connect devices such as computers, gaming consoles, and smart TVs.
Campus Networks: LANs are used in educational institutions to connect classrooms, libraries, and other facilities.
Industrial Networks: LANs are used in industrial settings to connect machines, sensors, and other devices.
LAN Technologies:
Ethernet: A popular LAN technology that uses twisted-pair or fiber optic cables to connect devices.
Wi-Fi: A wireless LAN technology that uses radio waves to connect devices.
Token Ring: A LAN technology that uses a token-passing protocol to manage data transmission.
Fiber Distributed Data Interface (FDDI): A LAN technology that uses fiber optic cables to connect devices.
In summary, LANs are computer networks that span a small geographic area, providing high-speed data transfer rates and low latency. They are commonly used in office buildings, homes, and educational institutions, and are suitable for applications that require fast data transfer and reliability.
Wide Area Network (WAN)
A Wide Area Network (WAN) is a computer network that spans a large geographic area, such as a city, state, or country. It is a type of network that connects devices and networks over a long distance, allowing them to communicate with each other and share resources.
Characteristics of WAN:
Geographic Scope: WANs typically cover a large area, such as a city, state, or country.
Number of Devices: WANs can connect a large number of devices, ranging from thousands to millions.
Data Transfer Rate: WANs have slower data transfer rates compared to LANs, typically in the range of 1.5 Mbps to 100 Mbps.
Network Topology: WANs often use a mesh or hybrid topology, where devices are connected to each other through multiple paths.
Network Protocol: WANs use protocols such as TCP/IP, ATM, and Frame Relay to manage data transmission.
Types of WAN:
Point-to-Point WAN: A point-to-point WAN connects two devices directly, using a dedicated link.
Multipoint WAN: A multipoint WAN connects multiple devices, using a shared link.
Virtual Private Network (VPN) WAN: A VPN WAN uses encryption and tunneling to create a secure and private network over a public network.
Satellite WAN: A satellite WAN uses satellite communication to connect devices over a long distance.
Advantages of WAN:
Wide Coverage: WANs provide wide coverage, making it possible to connect devices and networks over a large geographic area.
Cost-Effective: WANs can be cost-effective, as they eliminate the need for dedicated lines and reduce the cost of data transmission.
Scalability: WANs are highly scalable, making it easy to add new devices and networks as needed.
Flexibility: WANs offer flexibility, as they can be used to connect different types of devices and networks.
Disadvantages of WAN:
Slow Data Transfer Rates: WANs have slower data transfer rates compared to LANs, which can impact performance.
High Latency: WANs have higher latency compared to LANs, which can impact real-time applications.
Security Risks: WANs are more vulnerable to security risks, as they use public networks and are exposed to external threats.
Complexity: WANs can be complex to manage and maintain, as they require specialized equipment and expertise.
Real-World Applications of WAN:
Internet: The internet is a global WAN that connects devices and networks over a large geographic area.
Business Networks: WANs are used by businesses to connect offices, branches, and remote locations.
Government Networks: WANs are used by government agencies to connect offices, departments, and remote locations.
Telecommunications: WANs are used by telecommunications companies to provide services such as voice, data, and video.
WAN Technologies:
MPLS (Multiprotocol Label Switching): A WAN technology that uses label switching to manage data transmission.
VPN (Virtual Private Network): A WAN technology that uses encryption and tunneling to create a secure and private network.
ATM (Asynchronous Transfer Mode): A WAN technology that uses cell switching to manage data transmission.
Frame Relay: A WAN technology that uses frame switching to manage data transmission.
In summary, WANs are computer networks that span a large geographic area, providing wide coverage and scalability. They are commonly used by businesses, government agencies, and telecommunications companies to connect devices and networks over a long distance. While WANs have slower data transfer rates and higher latency compared to LANs, they offer flexibility and cost-effectiveness, making them a popular choice for many applications.
MAN: Metropolitan Area Network (MAN)
A Metropolitan Area Network (MAN) is a computer network that spans a metropolitan area, such as a city or town. It is a type of network that connects devices and networks within a limited geographic area, typically within a radius of 50 kilometers.
Characteristics of MAN:
Geographic Scope: MANs typically cover a metropolitan area, such as a city or town.
Number of Devices: MANs can connect a large number of devices, ranging from thousands to millions.
Data Transfer Rate: MANs have high data transfer rates, typically in the range of 100 Mbps to 10 Gbps.
Network Topology: MANs often use a ring or mesh topology, where devices are connected to each other through multiple paths.
Network Protocol: MANs use protocols such as Ethernet, Wi-Fi, and SONET to manage data transmission.
Types of MAN:
Cable MAN: A cable MAN uses coaxial cables to connect devices and networks.
Fiber MAN: A fiber MAN uses fiber optic cables to connect devices and networks.
Wireless MAN: A wireless MAN uses radio waves to connect devices and networks.
Hybrid MAN: A hybrid MAN uses a combination of different technologies, such as cable, fiber, and wireless, to connect devices and networks.
Advantages of MAN:
High-Speed Data Transfer: MANs provide high-speed data transfer rates, making them suitable for applications that require fast data transfer.
Reliability: MANs are generally more reliable than WANs, as they are less prone to errors and disruptions.
Scalability: MANs are highly scalable, making it easy to add new devices and networks as needed.
Cost-Effective: MANs can be cost-effective, as they eliminate the need for dedicated lines and reduce the cost of data transmission.
Disadvantages of MAN:
Limited Geographic Scope: MANs are limited to a metropolitan area, making them less suitable for applications that require wide area coverage.
Complexity: MANs can be complex to manage and maintain, as they require specialized equipment and expertise.
Security Risks: MANs are more vulnerable to security risks, as they use public networks and are exposed to external threats.
Interoperability: MANs can have interoperability issues, as different devices and networks may use different protocols and technologies.
Real-World Applications of MAN:
City Networks: MANs are used by cities to connect government offices, schools, and other public institutions.
University Networks: MANs are used by universities to connect campuses, libraries, and research centers.
Business Networks: MANs are used by businesses to connect offices, branches, and remote locations.
Telecommunications: MANs are used by telecommunications companies to provide services such as voice, data, and video.
MAN Technologies:
Ethernet: A MAN technology that uses twisted-pair or fiber optic cables to connect devices.
Wi-Fi: A MAN technology that uses radio waves to connect devices.
SONET (Synchronous Optical Network): A MAN technology that uses fiber optic cables to connect devices.
DWDM (Dense Wavelength Division Multiplexing): A MAN technology that uses fiber optic cables to connect devices and multiplex multiple signals onto a single fiber.
In summary, MANs are computer networks that span a metropolitan area, providing high-speed data transfer rates and reliability. They are commonly used by cities, universities, businesses, and telecommunications companies to connect devices and networks within a limited geographic area. While MANs have limited geographic scope and complexity, they offer scalability, cost-effectiveness, and high-speed data transfer rates, making them a popular choice for many applications.
Network Devices
Network devices are hardware or software components that connect, manage, and control data transmission between devices on a network. They play a crucial role in ensuring that data is transmitted efficiently, reliably, and securely. Here are some common network devices, their uses, and a detailed study of each:
Router
Use: Connects multiple networks together, routes traffic between them, and manages network traffic.
Study: Routers use routing protocols to determine the best path for data transmission. They also perform network address translation (NAT) to allow multiple devices to share a single public IP address.
Switch
Use: Connects multiple devices within a network, forwards data packets between them, and manages network traffic.
Study: Switches use MAC addresses to forward data packets to the intended recipient. They also perform packet switching, which allows multiple devices to share the same network connection.
Hub
Use: Connects multiple devices within a network, broadcasts data packets to all connected devices, and manages network traffic.
Study: Hubs are simple network devices that broadcast incoming data packets to all connected devices. They do not perform any routing or switching functions.
Bridge
Use: Connects two or more networks together, forwards data packets between them, and manages network traffic.
Study: Bridges use MAC addresses to forward data packets between networks. They also perform packet filtering, which allows them to block or forward data packets based on specific criteria.
Gateway
Use: Connects a network to the internet, manages network traffic, and provides security features such as firewalling and NAT.
Study: Gateways use routing protocols to determine the best path for data transmission. They also perform network address translation (NAT) to allow multiple devices to share a single public IP address.
Modem
Use: Connects a network to the internet via a dial-up or broadband connection, manages network traffic, and provides security features such as encryption.
Study: Modems use modulation and demodulation techniques to transmit data over phone lines or other communication media. They also perform error correction and flow control to ensure reliable data transmission.
Network Interface Card (NIC)
Use: Connects a device to a network, manages network traffic, and provides security features such as encryption.
Study: NICs use MAC addresses to identify devices on a network. They also perform packet switching, which allows multiple devices to share the same network connection.
Wireless Access Point (WAP)
Use: Connects wireless devices to a network, manages network traffic, and provides security features such as encryption.
Study: WAPs use wireless communication protocols such as Wi-Fi to connect devices to a network. They also perform packet switching, which allows multiple devices to share the same network connection.
Firewall
Use: Blocks unauthorized access to a network, manages network traffic, and provides security features such as packet filtering and NAT.
Study: Firewalls use packet filtering to block or forward data packets based on specific criteria. They also perform network address translation (NAT) to allow multiple devices to share a single public IP address.
Network Attached Storage (NAS)
Use: Provides shared storage for devices on a network, manages network traffic, and provides security features such as encryption.
Study: NAS devices use file systems such as NFS or SMB to provide shared storage for devices on a network. They also perform packet switching, which allows multiple devices to share the same network connection.
In-Depth Study of Network Devices
Here is a more detailed study of each network device:
Router
Routing protocols: RIP, OSPF, EIGRP, BGP
Network address translation (NAT): static NAT, dynamic NAT, PAT
Packet switching: store-and-forward, cut-through
Switch
MAC address table: learning, aging, flooding
Packet switching: store-and-forward, cut-through
VLANs: VLAN tagging, VLAN trunking
Hub
Broadcast domain: collision domain, broadcast storm
Packet switching: simple packet switching
Bridge
MAC address table: learning, aging, flooding
Packet switching: store-and-forward, cut-through
Spanning tree protocol: STP, RSTP, MSTP
Gateway
Routing protocols: RIP, OSPF, EIGRP, BGP
Network address translation (NAT): static NAT, dynamic NAT, PAT
Packet switching: store-and-forward, cut-through
Modem
Modulation techniques: AM, FM, PM, QAM
Demodulation techniques: AM, FM, PM, QAM
Error correction: FEC, ARQ
Network Interface Card (NIC)
MAC address: OUI, NIC, MAC address table
Packet switching: store-and-forward, cut-through
VLANs: VLAN tagging, VLAN trunking
Wireless Access Point (WAP)
Wireless communication protocols: Wi-Fi, Bluetooth, Zigbee
Packet switching: store-and-forward, cut-through
Security features: WEP, WPA, WPA2, WPA3
Firewall
Packet filtering: stateful packet inspection, stateless packet inspection
Network address translation (NAT): static NAT, dynamic NAT, PAT
Security features: access control lists, intrusion detection systems
Network Attached Storage (NAS)
File systems: NFS, SMB, AFP
Packet switching: store-and-forward, cut-through
Security features: access control lists, encryption
Conclusion
In conclusion, network devices play a crucial role in ensuring that data is transmitted efficiently, reliably, and securely over a network. Each network device has its own unique features and functions, and understanding how they work is essential for designing, implementing, and managing a network. By studying the different types of network devices, their uses, and their features, network administrators can design and implement a network that meets the needs of their organization.